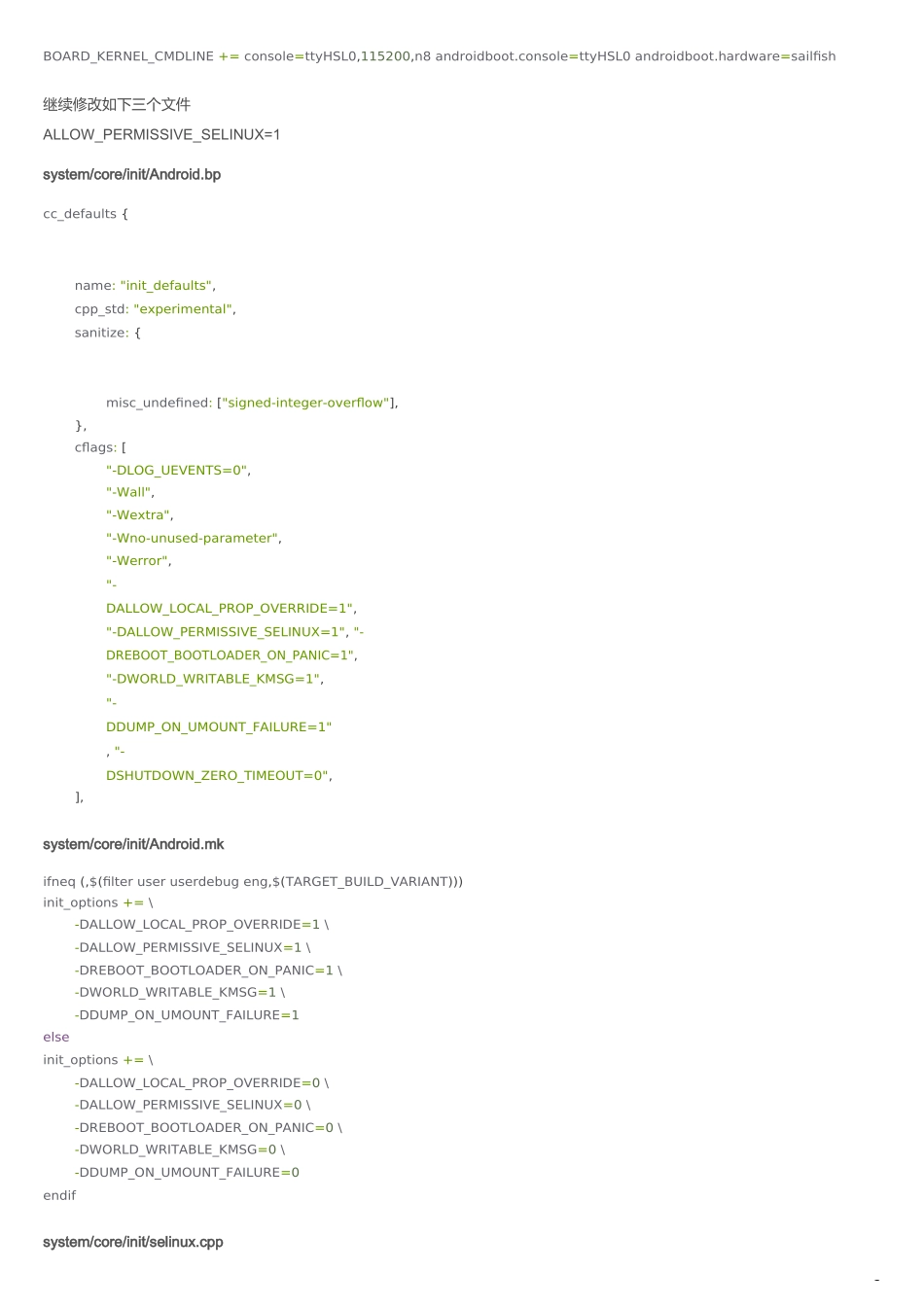
1android10.0(Q) root Pixel 1(QCOM 821) user 版本打开 root 权限前言个人玩家建议采用 magisk 方式直接修补 boot.img 实现 root 即可,然后搭载 RE 文件管理器可操作 system 相关分区源码玩家可直接修改 aosp 源码后自己编译 rom 直刷。文件清单aosp10\build\core\main.mk aosp10\system\sepolicy\definitions.mk aosp10\system\sepolicy\Android.mk aosp10\system\core\fs_mgr\Android.bp aosp10\system\core\adb\daemon\main.cpp aosp10\system\core\adb\Android.bpaosp10\system\core\init\selinux.cpp aosp10\system\core\init\Android.mk aosp10\system\core\init\Android.bp aosp10\device\google\marlin\sailfish\BoardConfig.mk1、让进程名称在 AS Logcat 中可见,通过修改 ro.adb.secure 和 ro.secureps:这步不是必须的,目的只是在 logcat 中可见进程 pid 和包名,而且打开 USB 调试时默认授权,不再弹授权框build/make/core/main.mktags_to_install :=ifneq (,$(user_variant))# Target is secure in user builds.-ADDITIONAL_DEFAULT_PROPERTIES += ro.secure=1+# ADDITIONAL_DEFAULT_PROPERTIES += ro.secure=1+ADDITIONAL_DEFAULT_PROPERTIES += ro.secure=0ADDITIONAL_DEFAULT_PROPERTIES += security.perf_harden=1ifeq ($(user_variant),user)-ADDITIONAL_DEFAULT_PROPERTIES += ro.adb.secure=1+# ADDITIONAL_DEFAULT_PROPERTIES += ro.adb.secure=1+ADDITIONAL_DEFAULT_PROPERTIES += ro.adb.secure=0endififeq ($(user_variant),userdebug)@@ -251,7 +253,7 @@ ifneq (,$(user_variant)) tags_to_install += debugelse# Disable debugging in plain user builds.-enable_target_debugging :=+# enable_target_debugging := endif# Disallow mock locations by default for user builds2、修改 SELinux 权限为 Permissivepixel 1 代号 sailfish,找到对应文件 BoardConfig.mk 增加 androidboot.selinux=permissivedevice/google/marlin/sailfish/BoardConfig.mk2BOARD_KERNEL_CMDLINE += console=ttyHSL0,115200,n8 androidboot.console=ttyHSL0 androidboot.hardware=sailfish继续修改如下三个文件ALLOW_PERMISSIVE_SELINUX=1system/core/init/Android.bpcc_defaults {name: "init_defaults", cpp_std: "...