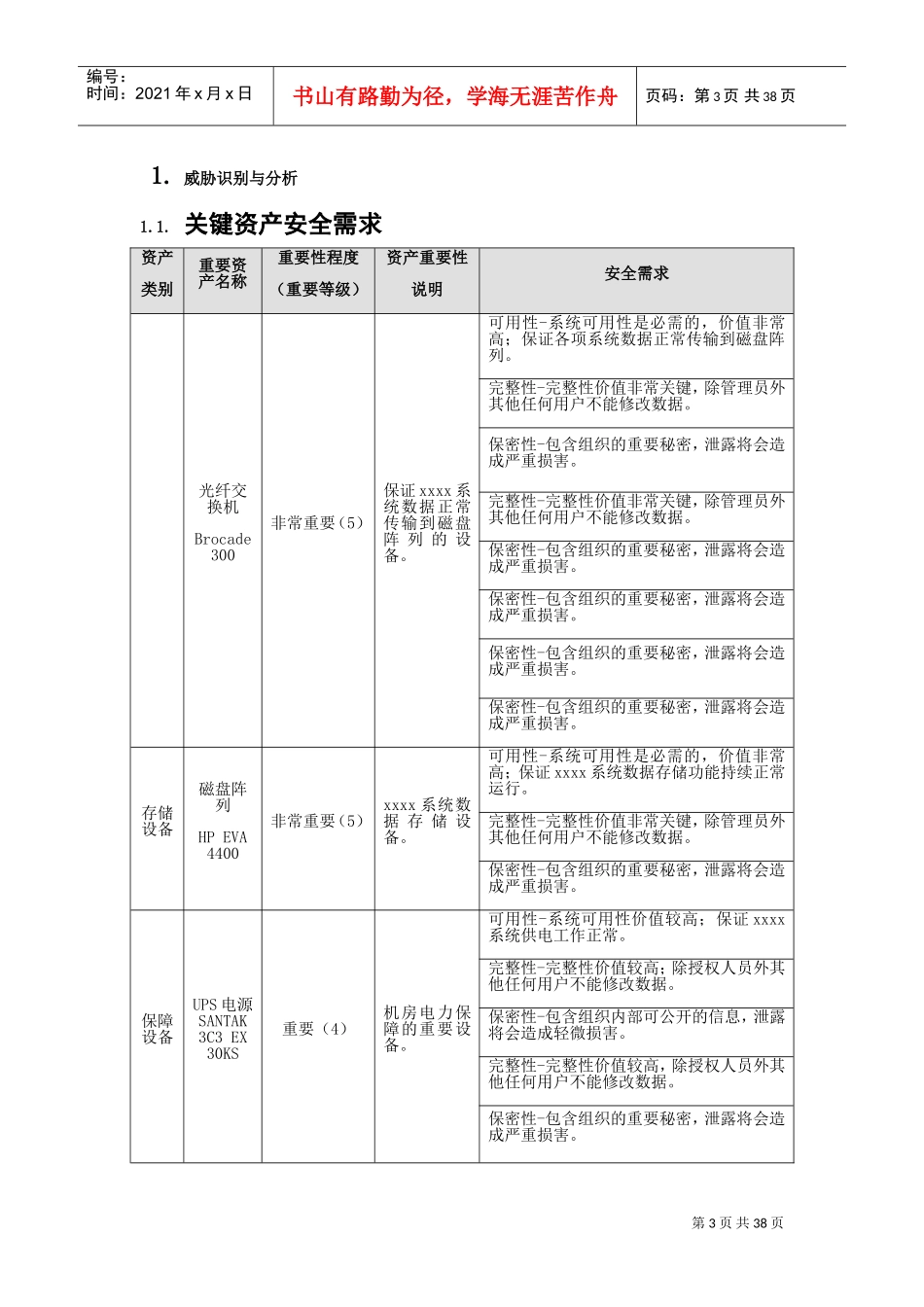
目录1.威胁识别与分析..................................................................................................................................21.1.关键资产安全需求......................................................................................................................21.2.关键资产威胁概要......................................................................................................................31.3.威胁描述汇总..............................................................................................................................91.4.威胁赋值....................................................................................................................................102.脆弱性识别与分析............................................................................................................................122.1.常规脆弱性描述........................................................................................................................122.1.1.管理脆弱性................................................................................................................122.1.2.网络脆弱性................................................................................................................122.1.3.系统脆弱性................................................................................................................122.1.4.应用脆弱性................................................................................................................122.1.5.数据处理和存储脆弱性............................................................................................122.1.6.运行维护脆弱性........................................................................................................122.1.7.灾备与应急响应脆弱性............................................................................................122.1.8.物理脆弱性................................................................................................................122.2.脆弱性专项检查........................................................................................................................122.2.1.木马病毒专项检查....................................................................................................122.2.2.服务器漏洞扫描专项检测........................................................................................122.2.3.安全设备漏洞扫描专项检测....................................................................................192.3.脆弱性综合列表........................................................................................................................213.风险分析............................................................................................................................................253.1.关键资产的风险计算结果........................................................................................................253.2.关键资产的风险等级................................................................................................................273.2.1.风险等级列表............................................................................................................273.2.2.风险等级统计...............................................................................................................